Last year, at DEF CON‘s Recon Village and Bsides Las Vegas, I gave a talk explaining a new OSINT technique to obtain a target’s phone number by knowing their email address.
Feel free to read the detailed post explaining the techniques or watch the talk.
If you insist on a TL;DR, I demonstrate how the lack of standardization in masking PII during the password reset process coupled with the knowledge of the Phone Numbering Plan of the target’s country, can be used to generate a list of valid phone numbers that are candidates to be the target’s number. This list can be used to bruteforce password reset attempts to find out the target’s true phone number.
Confused? Seriously, read the post or watch the talk before continuing.
A new OSINT tool
During the presentation, I demoed and later published email2phonenumber, a tool that automates the entire process described above.
This tool does 3 things for you:
- It scrapes websites to collect phone number digits from password reset attempts
- It generates a list of valid phone numbers using open source data published by the organization in charge of the countries Phone Numbering Plan
- It bruteforces password resets using the list of phone numbers and correlates the displayed partial email to a given one for a match
The tool is useful but I wrote it mostly as a PoC due to some caveats:
- As any OSINT tool, it tends to break constantly as it depends on the UI elements of many websites which tend to change over time.
- The capability to process and search data is limited since it does not rely on a DB.
- Scraping websites and launching bruteforce attempts can be done already with specialized tools like Burp’s intruder and wfuzz (also much more efficient).
I realized that instead of reinventing the wheel, I should focus on the novel aspect of my research, using the Phone Numbering Plan knowledge and open source data to create lists of valid phone numbers allowing:
Easy search based on masked phone numbers
You can provide the digits that you know only and fill remaining unknown digits with ‘?’. The tool should generate all the valid phone numbers based on that mask.
Advanced filtering
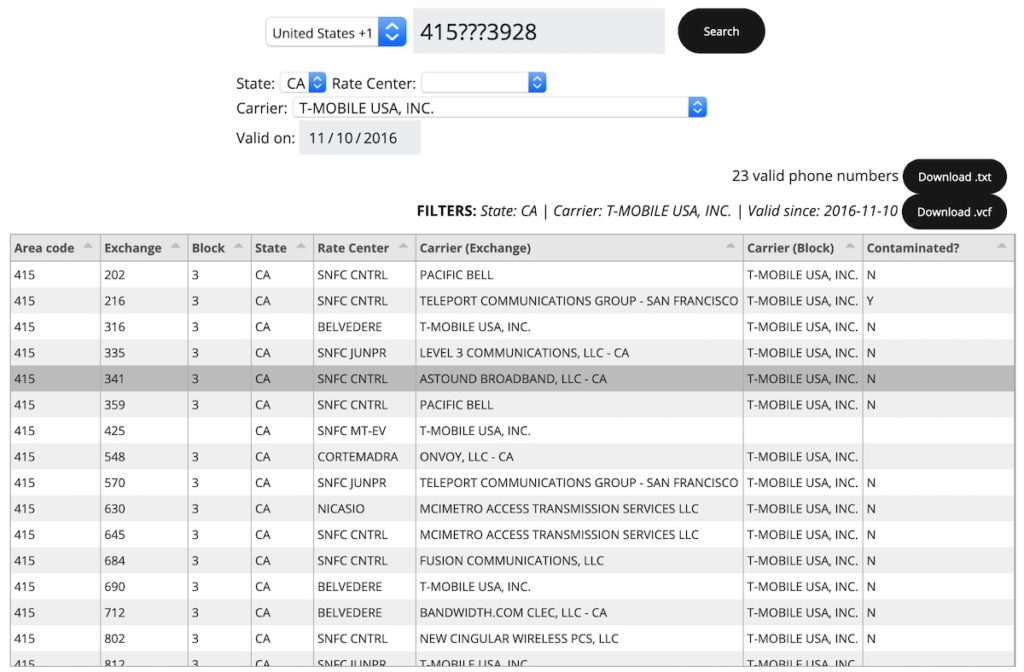
Support for multiple filters. For US numbers, you should be able to narrow your search by location (state and rate center), carrier and even the date since the phone number has been active.
Display of more information
The tool doesn’t just list valid phone numbers, it also includes the state, rate center, original carrier and if the range is contaminated (more on that later).
Multi-country support
Support for multiple countries. If you happen to know the official organizations that handle phone numbers in your country, please let me know and I may add support for it.
Download in multiple formats
This is a good one. I came across an interesting paper talking about “contact discovery” abuse. I was aware of this little OSINT trick but was glad to see an academic empirical study on the subject. Essentially, there are many apps and services that allow you to “share” your contacts in order to make it easier for you to find friends on that particular platform. For example, you can allow Telegram access to your contact list on your phone so you can see who has a Telegram account. Similarly, you can share your contacts with LinkedIn to find your colleagues easier. Basically, if you have someone’s phone number in your contact list, you can determine if that person has an account in multiple services and obtain some metadata.
As I am writing a tool that will provide a list of valid phone numbers based on your search criteria, why not add support to export the list as .vcf? This file format is standard for contacts and allows one to import the list of valid numbers as contacts to your test device. You may then sync it with any apps you think your target may be using to find the right number!
I mentioned during my talk that I was working on the tool and while it took longer than expected, it is finally here!
Phonerator
Phonerator is an online search engine that allows one to provide a few digits and generate a list of possible valid phone numbers. It also allows one to further narrow the search by providing carriers, date of service, physical location, exchange, etc.
Lastly, you may download a dictionary text file with all possible numbers to be used with other tools.
Architecture
Phonerator has 3 components:
- Spider: A script that periodically downloads and parses information from official organizations in charge of the Phone Numbering Plan of different countries that make such data public.
- Backend: A database fed by the script which contains the millions of records organized and optimized for search
- Frontend: A simple website that allows users to make advanced searches, display all the phone number information and allows the download of valid phone numbers lists
Use cases
To illustrate how Phonerator can be beneficial to OSINT professionals, private investigators, researchers, red teamers and potentially to you, I list a number of hypothetical use cases. Take them with a grain of salt.
Stalker
You are the victim of a stalker that keeps creating email accounts to send you death threats. They use sock puppet accounts on different email providers to make sure you are not automatically deleting the emails.
You receive an email from a Yahoo account:
You know that Yahoo’s password reset page leaks the first digit and the last two, so you use the email address to initiate a password reset. Having the first digit, you use Phonerator to get a list of possible states the person may be from. You discard all numbers that have the area code + exchange correspond to carriers that are not major mobile carriers (AT&T, Verizon, T-Mobile and Sprint). The list of phone numbers gets reduced significantly, so you download the list and use it with Twilio’s whitepages Add-on to do a reverse search and obtain the owners information of those numbers.
You look through the list and among the many records you recognize one person…
Red Team exercise
You have your target’s email address and need to access his inbox to launch a credible spearphishing campaign against other employees at the company you are testing. You look up his email in Dehashed and find credentials to other sites he used in the past. Like ~80% of Internet users, he is using the same password everywhere. You login into the target’s email provider but you get challenged for 2FA. Time to phish the target for the 2FA code, but to do so, you need the phone number…
Using services like namechk, you find his Paypal account and LinkedIn. The Paypal reset password page leaks 5 digits, the first one and the last 4. You look up the email address in one of the many data brokers but no luck, you only find the address where he lives. You use Phonerator‘s filters to indicate the State.
LinkedIn says that the target has been an employee at the company for 7 years now. You make the assumption that his work number has probably never changed so you use Phonerator to discard all numbers in which area code + exchange combination was assigned to a carrier in the last 6 years ago or less. The last step is to download the list of remaining valid phone numbers from Phonerator in .vcf format to leverage services that allow finding people by phone number. You go over the list of profile pictures and names looking for a match.
Finding interesting carriers
There are over 3,000 registered carriers in the United States, but the general public is usually only aware of the 4 big ones: AT&T, Verizon, T-Mobile and Sprint. So… what are all the others about? You can use Phonerator to get the full list of currently registered carriers in different countries and pick the ones that sound interesting for further investigation. For example:
- Sattelink Paging, Inc.: Carrier from a company specialized in Satellite communications
- Smart City Solutions II, LLC: “America’s leading provider of state-of-the art technology services to convention centers, sports and live entertainment arenas and stadiums, trade shows and events”.
I am wondering what some good oldskool wardialing to these carrier’s valid phone number list could find…
Demo
Limitations
Phonerator is not perfect, because the data is not perfect. You may be looking for a target which you know is an AT&T customer so you use Phonerator‘s carrier filter to discard all numbers that are not from AT&T. There are 2 problems here.
Portability
Customers can change carriers while keeping their numbers. This is also known as “porting” your number. NANPA‘s data only takes into account which carriers have specific area code + exchange ranges assigned originally. If a customer ports a number to a different carrier in that range, NANPA does not track it. The exception is if the carrier “donates” back the entire range to be reassigned by NANPA to a different carrier. In this case, we are talking about “contamination“.
Per public slides on their site:
Contamination means that at least one telephone number within a thousands-block is not available for assignment to end users or customers. Blocks contaminated up to and including 10 percent are eligible for donation. A telephone number is “not available for assignment” if it is classified as administrative, aging, assigned, intermediate, or reserved as defined in FCC rules (FCC 00-104, §52.7 (h)).
All contaminated numbers in blocks that are being donated must be Intra-Service Provider Ported in NPAC prior to the block being donated
NPAC is the US administration in charge of managing phone numbers portability. I recommend reading through their documentation, great resource for further research into the US telephone system.
The Neustar glosary page defines contamination as:
“Contamination” refers to the fact that some telephone numbers are already working when a block is available for assignment. As a result, not all the telephone numbers in the block are available to the new block-owner for its use. (As these existing customers disconnect their service over time, the now-vacant telephone numbers are returned to the block-owner for its use.).
That said, there is good news. The US National Pooling Administration does “somewhat” track it. We can see if a particular block is “contaminated” and even by how many numbers.
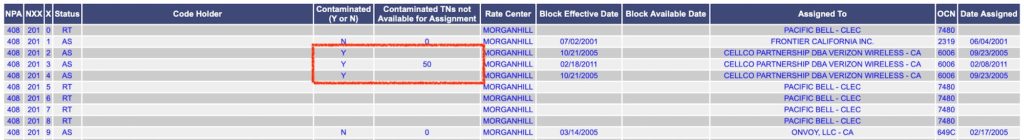
Say we have our target’s first 3 digits and last 4. In other words, we have the area code and the block number. Before using Phonerator to filter out numbers that are not assigned to AT&T, check if there are area code + exchange + blocknumber combinations that are contaminated. If so, don’t filter those out as it may be assigned to a different carrier but can contain “contaminated” numbers belonging to AT&T, including your target’s number.
There are many (and free) resources to query the real carrier of a phone number.
*Pro-tip: Many carriers are vulnerable to user enumeration. You may be able to use your target’s email address to find out which carrier he is using ;)
Acquisitions, Resellers and out of business
Many carriers on NANPA’s database date from the 80s and are not in business anymore. The big ones like AT&T and Verizon have “acquired” many of the phone number ranges assigned to those old carriers yet NANPA does not provide information about it. Those ranges are still “assigned” to the old carriers. The same can happen with big resellers like LEVEL 3 Communications. Same goes for big carriers buying others like AT&T acquiring Cingular.
This means that you need to be mindful of this when using the carrier filter. You may be filtering out ranges currently assigned to a major carrier by filtering out old carriers. It is in my TODO to add a “combined” filter for major carriers. You then will be able to pick “AT&T” and it will automatically include Cingular and others that belong to AT&T nowadays. This does require extensive knowledge of carriers and its history which I don’t have, so feel free to reach out if you do.
Other interesting tidbits
As I went through the effort of gathering, structuring and storing all the information in a database, I thought I’d write some queries to provide more insight into the American phone numbering system.
As of this writing:
- There are 3,771 carriers registered in the NANPA territories.
- The rate center with most phone numbers assigned is “NWYRCYZN01” which corresponds to Verizon in the area of Manhattan and handles the 212, 646 and 917 area codes.
- The most common area code is 347 and the least common is 684 which corresponds the islands of Tutuila, Aunuʻu, Ofu, Olosega, Taʻū, Swains Island, and Rose Atoll in American Samoa.
- The most common exchange for valid phone numbers is 200, the least is 700.
- The most common block number for pooled numbers is ‘0‘, ‘5′ is the least common
- There is no exchange ending in ‘11‘. In other words, there is no phone number which 5th and 6th digit is ‘11‘ (nor is there any exchange between 000 and 199).
*Pro-tip: It is common for websites to demand a phone number when you register even though many times there is no reason for it. Provide an invalid phone number so you don’t leak yours or run the risk of someone else receiving information about your account. Simply remember to set the exchange to a number below 200. (415-025-1823).
CTF
I created a small OSINT challenge that requires the use of Phonerator so you can get a taste of its potential :).
Where in the world is Carmen Sandiego?
Carmen has escaped again and I need your help to locate her. Thanks to my friends at NSA I got access to the SS7 network and I can find her if we obtain her phone number. They were able to obtain a leak from a secure communications service she was using that contained her email address and a hashed version of her phone number + city she connected from. Unfortunately, it was hashed with 5 million rounds of PBKDF2. We estimate that bruteforcing in a reasonable amount of time is only feasible having the correct city and less than 500 numbers.
Email: carm3n5andi3go@martinvigo.com
Hashed phone number: a599f5e85a15799c5fa0a11887dbfc9ebd4de92e0ebbac6768dec60377454ab1
Algorithm used to hash phone numbers:
#!/usr/bin/python3 import hashlib import binascii ## # Takes phonenumber without country code nor spaces. Example: 5551234567 # Takes city lowercase without spaces. Example: sanfrancisco ## def get_phone_hash(phonenumber, city): stringInput = phonenumber + city; binhash = hashlib.pbkdf2_hmac('sha256', stringInput.encode("utf-8"), b'', 5000000); return binhash.hex();CAUTION: The NSA warned me that OPSEC is utterly important. Do not attempt to reset any password. It won’t help you find any useful information and she will know we are tracking her.
Find her phone number!
The flag is Carmen Sandiego’s phone number. Send me a DM on Twitter with the number and I’ll give you street credit ;)








